Firewall Traffic Flow Diagram
Filtering centralized firewall deploy 10 critical steps to survive a ransomware attack, step 4: configure Packet flow through an asa firewall
AN-0062-EN – Stateful firewalls, IPS, IDS and UTM load balancing
Firewall — zentyal 2.2 documentation Asa packet flow cisco firewall traffic diagram inspection steps forward series through Deploy centralized traffic filtering using aws network firewall
Firewall location and configuration
Flow firewall asa packet throughDevelopment of a software based firewall system for computer network Palo alto flow traffic packet firewall path security sequence os pan reference firewalls handleFirewall definition.
Firewall location configuration used routing traffic based where community firewalls jisc internet backup route policy figureFirewall flow chart system software figure interface traffic network computer How firewalls (security gateways) handle the packets? (traffic flowAn-0062-en – stateful firewalls, ips, ids and utm load balancing.

Series of steps to forward a packet in a cisco asa firewall
Fortigate flow packet firewallIps ids load stateful utm balancing firewalls firewall balancer static flows What is firewall? definition, functions, benefits, types, and how itFirewall zentyal schema network security illustrating traffic flows different.
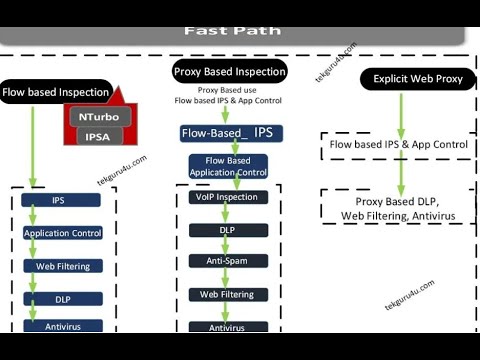
Deployment models for aws network firewallFirewall deployment deployed subnet workload Fortigate firewall packet flow5 traffic flow diagram.

Firewall diagram traffic ransomware survive critical outbound configure attack steps filter step
.
.